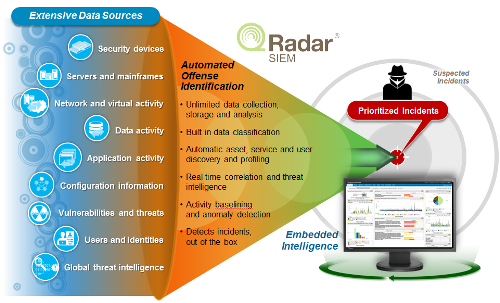
Sycope about Network flow monitoring – a valuable source of data for SIEM systems || Jacek Grymuza || Jun 26, 2022

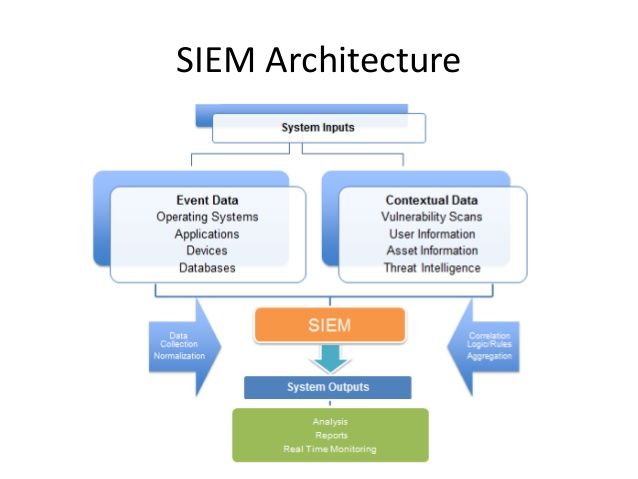
What Is Security Information and Event Management (SIEM)? Definition, Architecture, Operational Process, and Best Practices | Spiceworks It Security
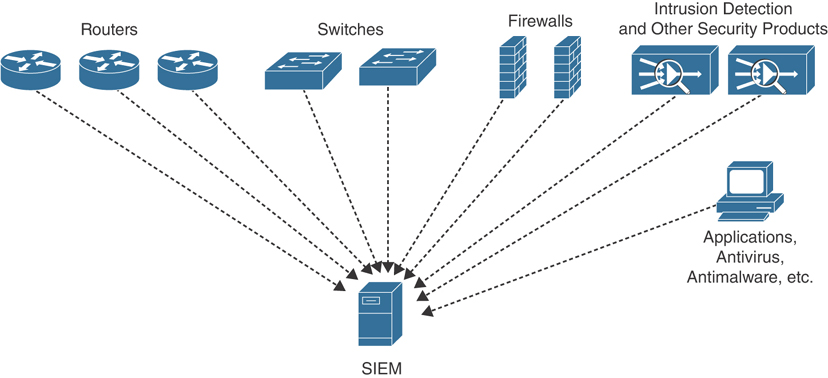
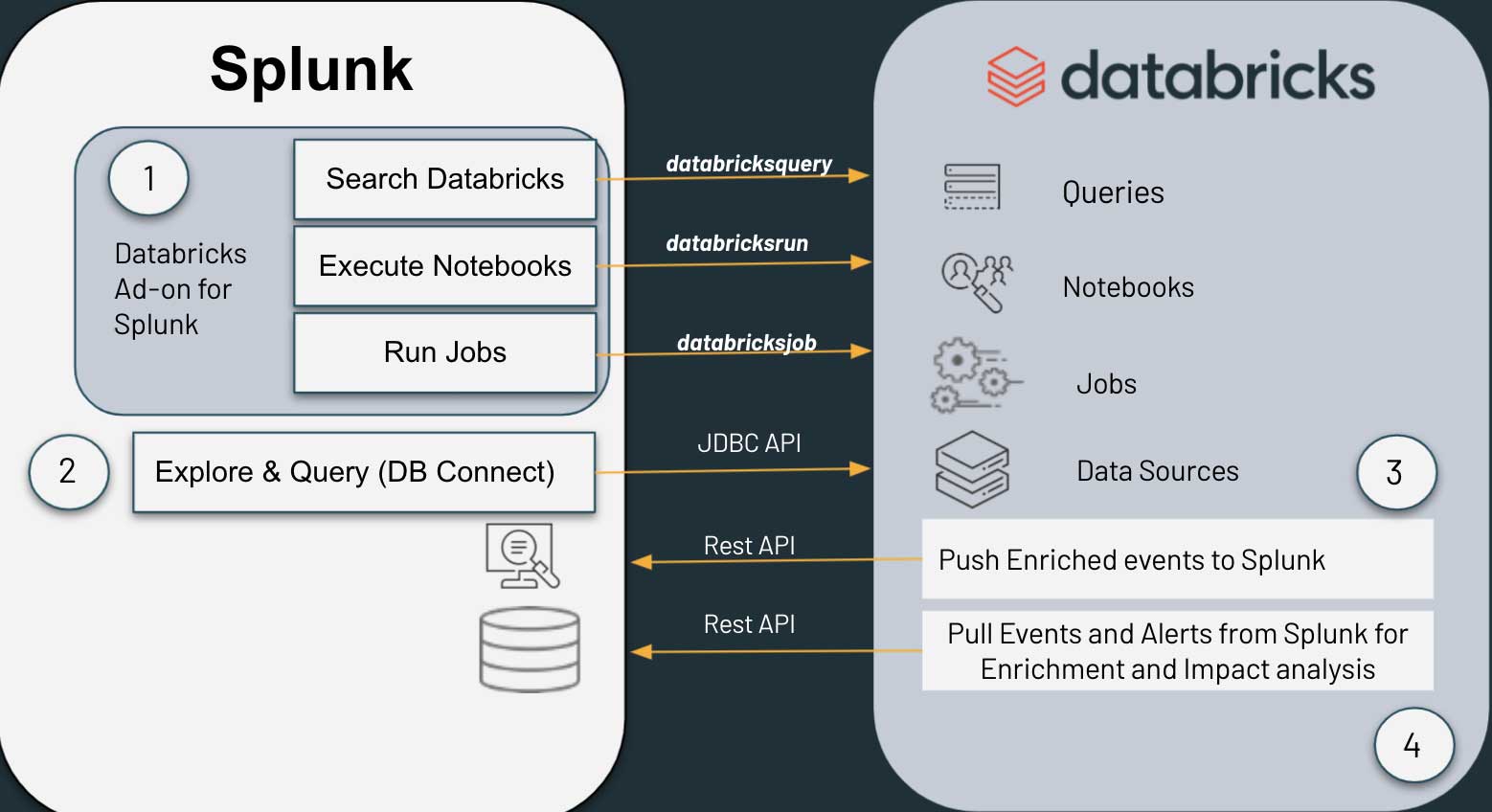
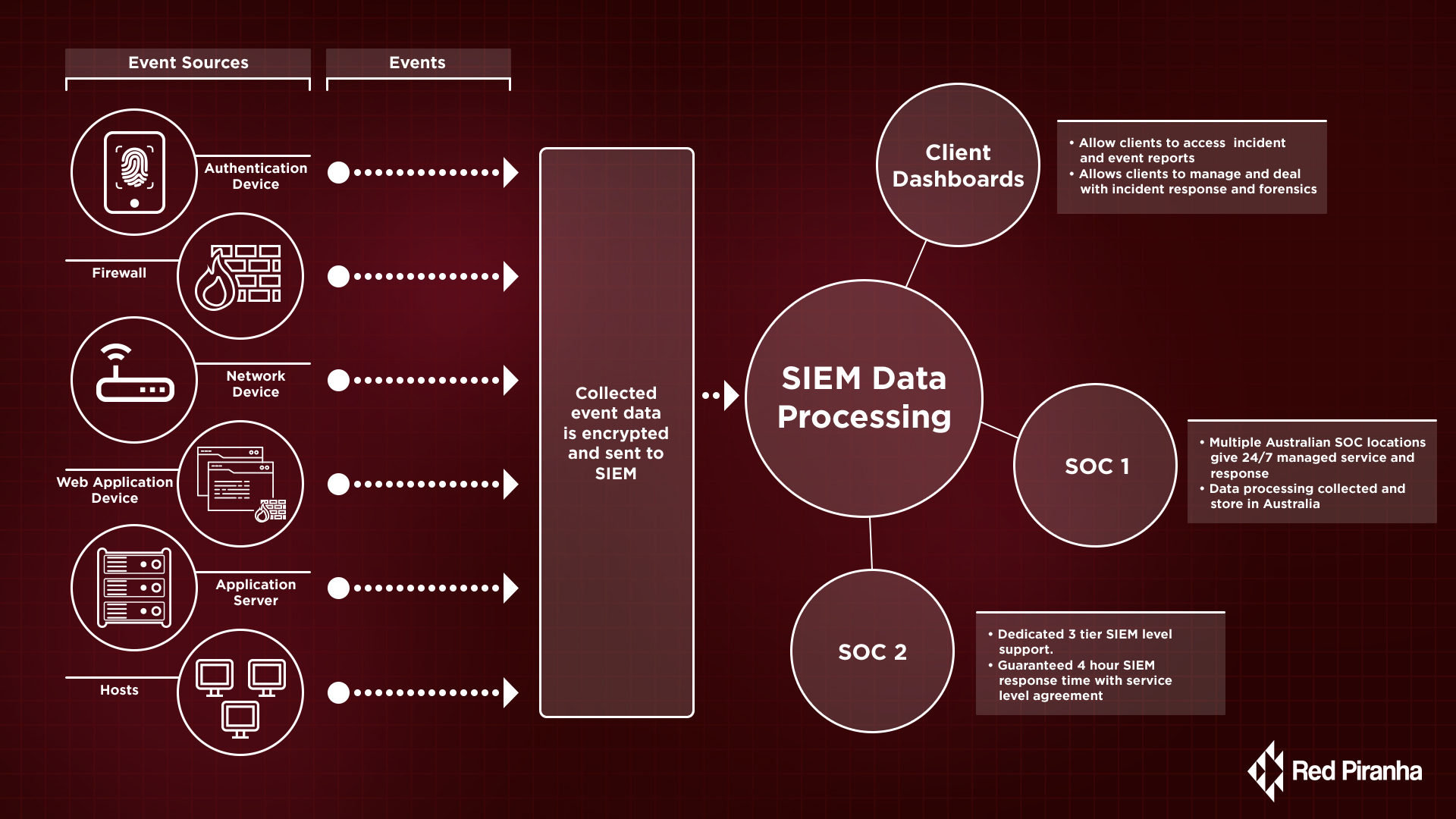

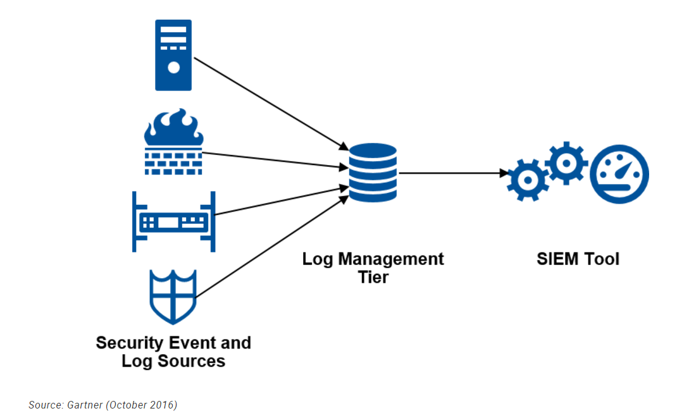
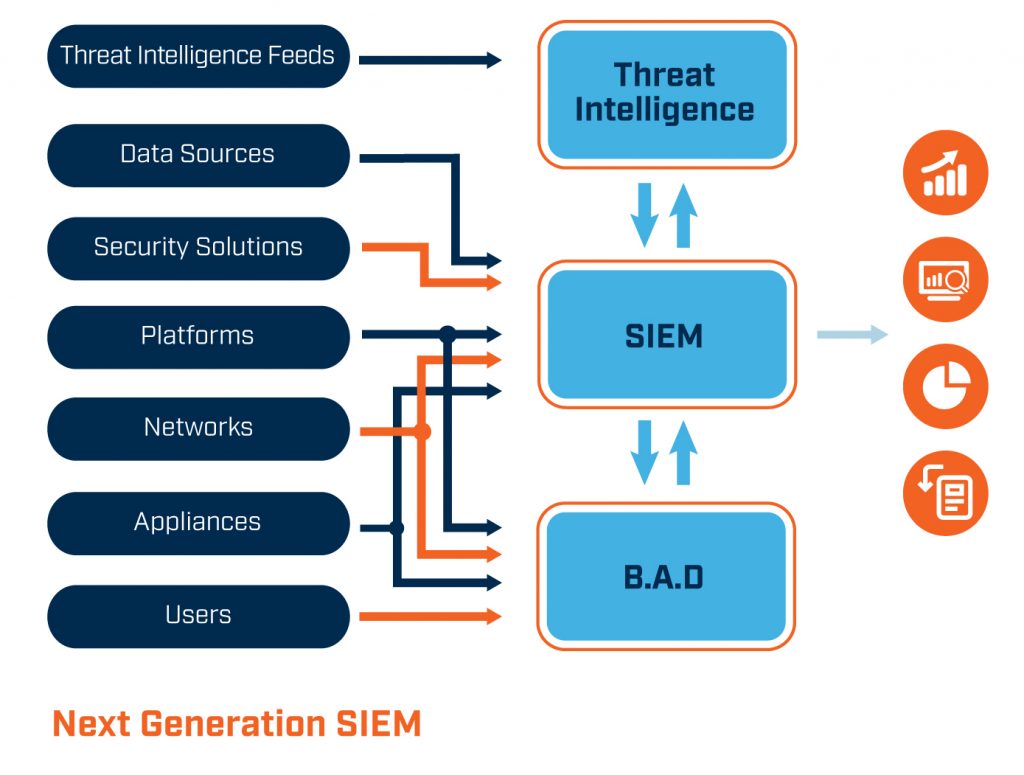
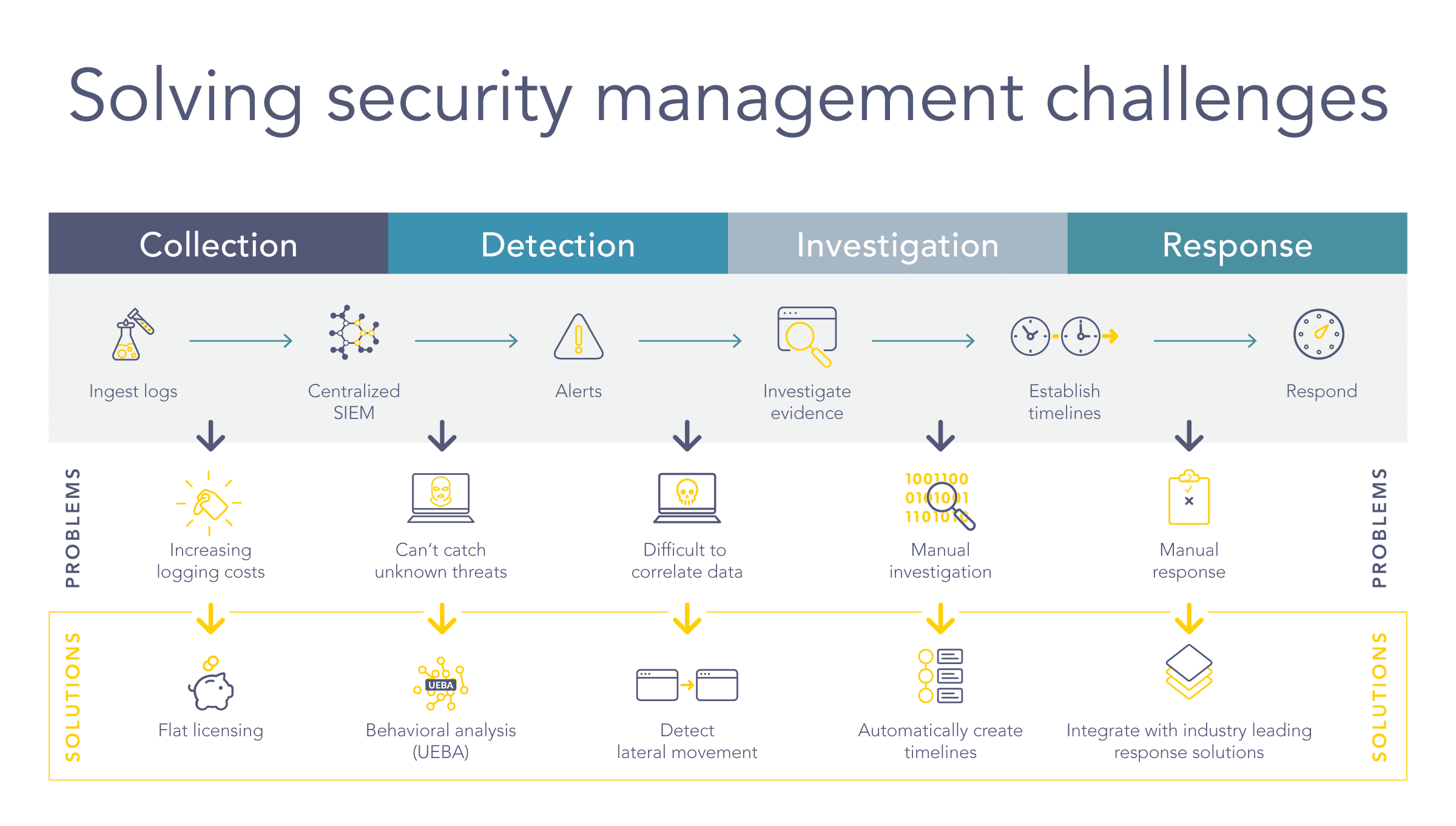






![Data Sources for Insider Threat Detection [44] | Download Scientific Diagram Data Sources for Insider Threat Detection [44] | Download Scientific Diagram](https://www.researchgate.net/publication/341103351/figure/fig3/AS:886738146840585@1588426257678/Data-Sources-for-Insider-Threat-Detection-44.jpg)