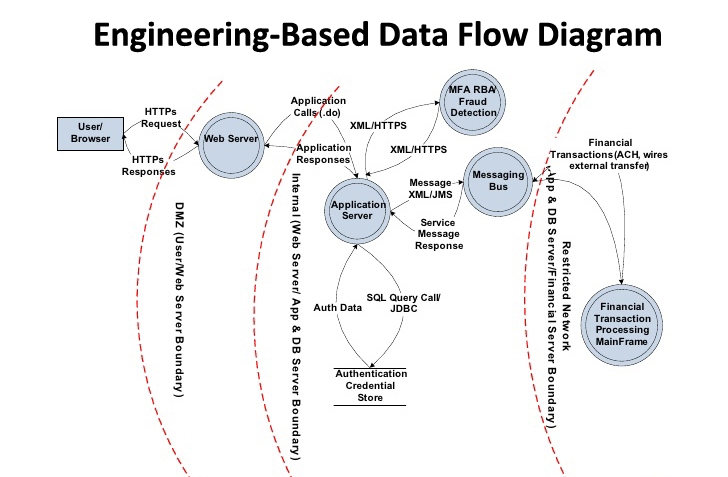
SECURITY IN THE DESIGN PHASE. Security is important in every stage of… | by WORTH Internet Systems | Medium

How to Create a Network Security Diagram Using ConceptDraw PRO | Flowcharts | Audit Flowcharts | Diagram Of Flow Charts Of Computer Security
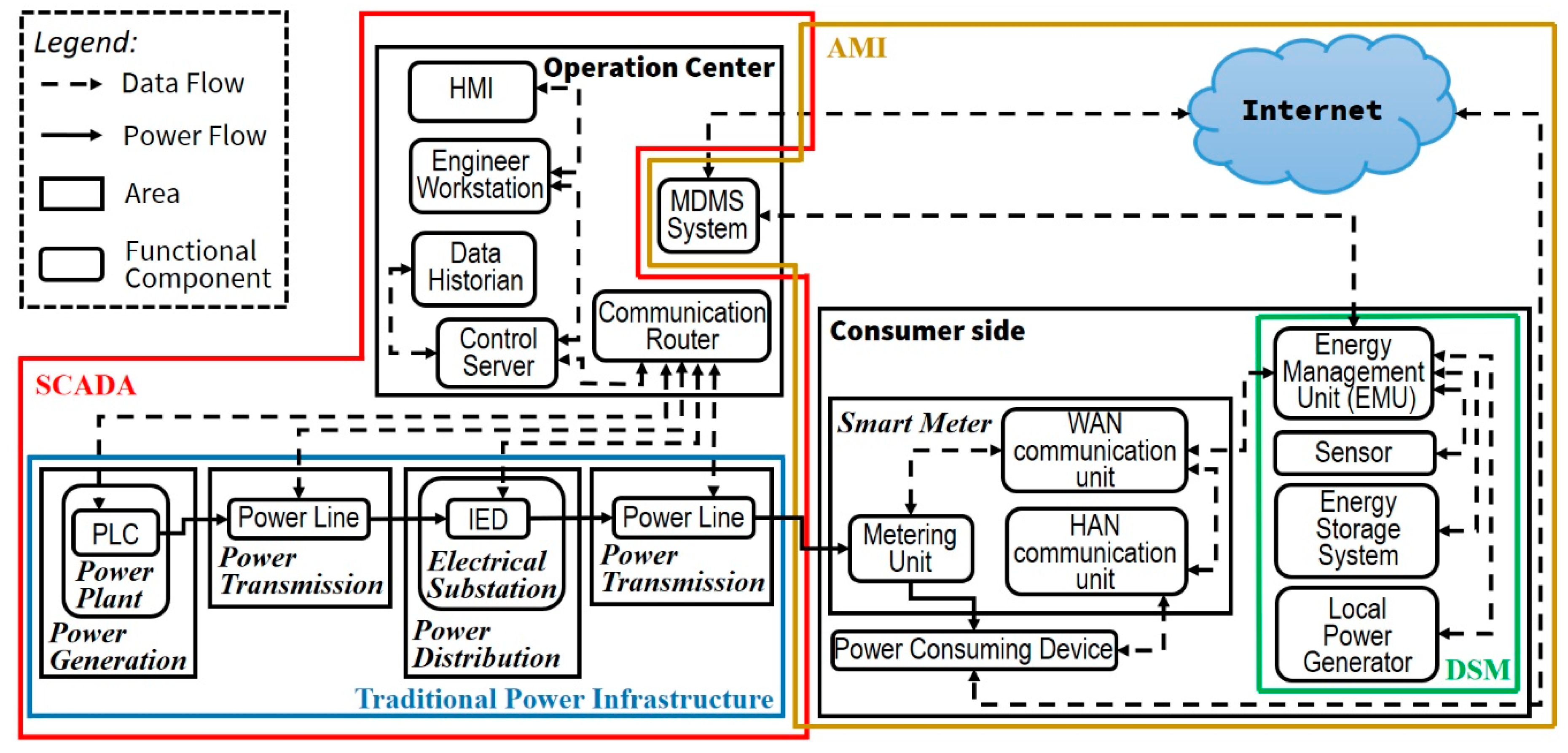
Inventions | Free Full-Text | Determining Information Security Threats for an IoT-Based Energy Internet by Adopting Software Engineering and Risk Management Approaches
![PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b1ef84599ca7a255bbf98822e25970d69ad49dac/4-Figure1-1.png)
PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar