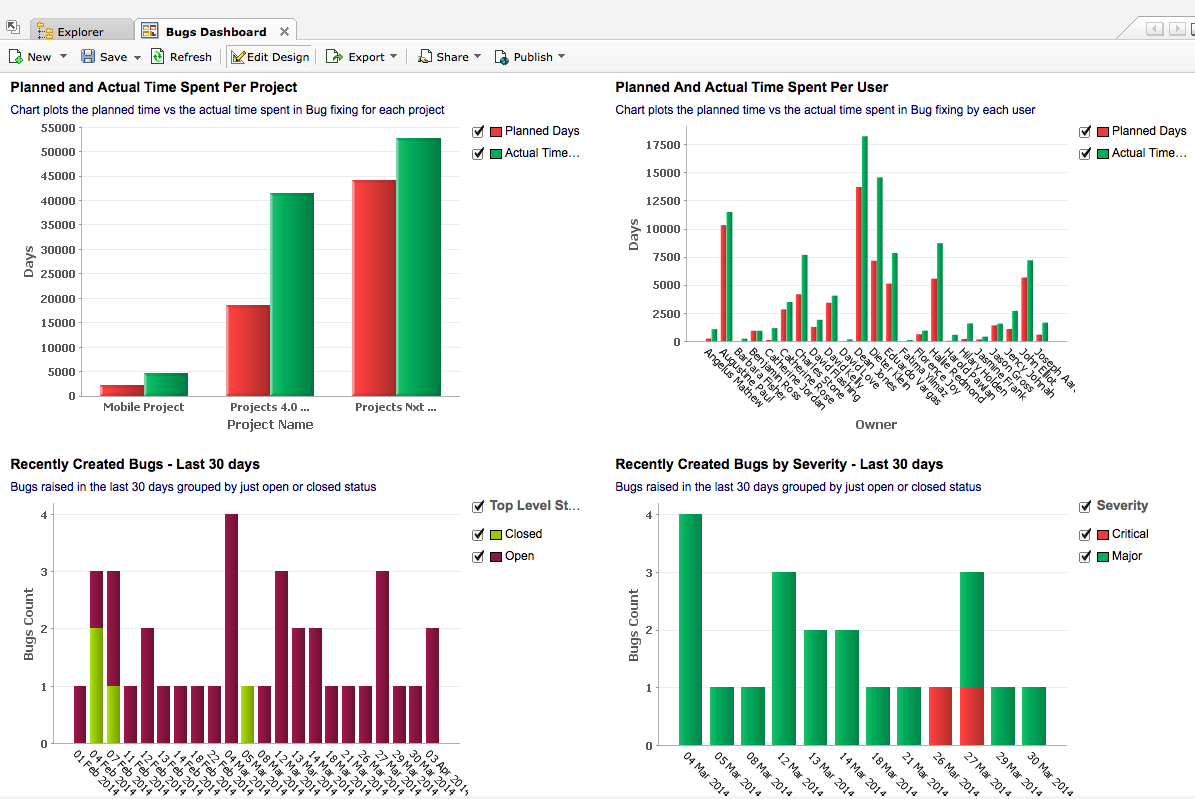
Automating the Search for 'Silent' Software Bugs - The Data Science Institute at Columbia University
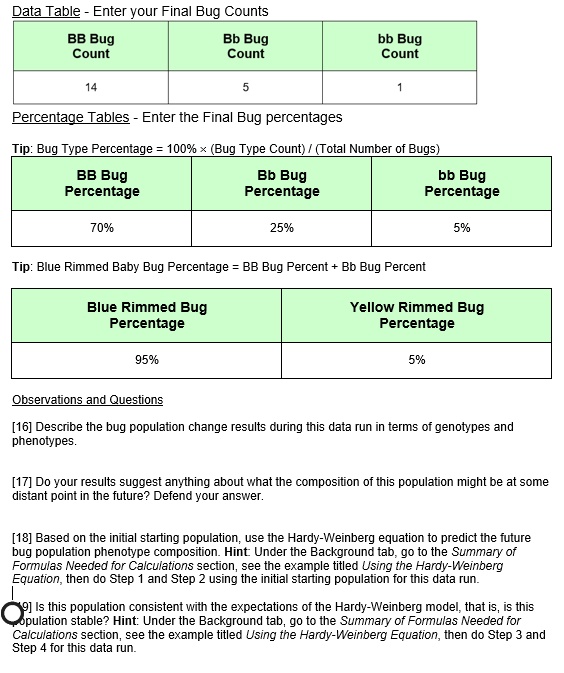
SOLVED: Data Table Enter vour Fina Bug counts BB Bug Count Bb Bug Count bb Bug Count PercentageTables Enter the Final Bug percentages Tip: Bug Type Percentage 10080 Bug Type Count) (Total

Illustration of bugs or insects crawling over binary computer data code to illustrate a computer software bug or computer virus Stock Photo - Alamy
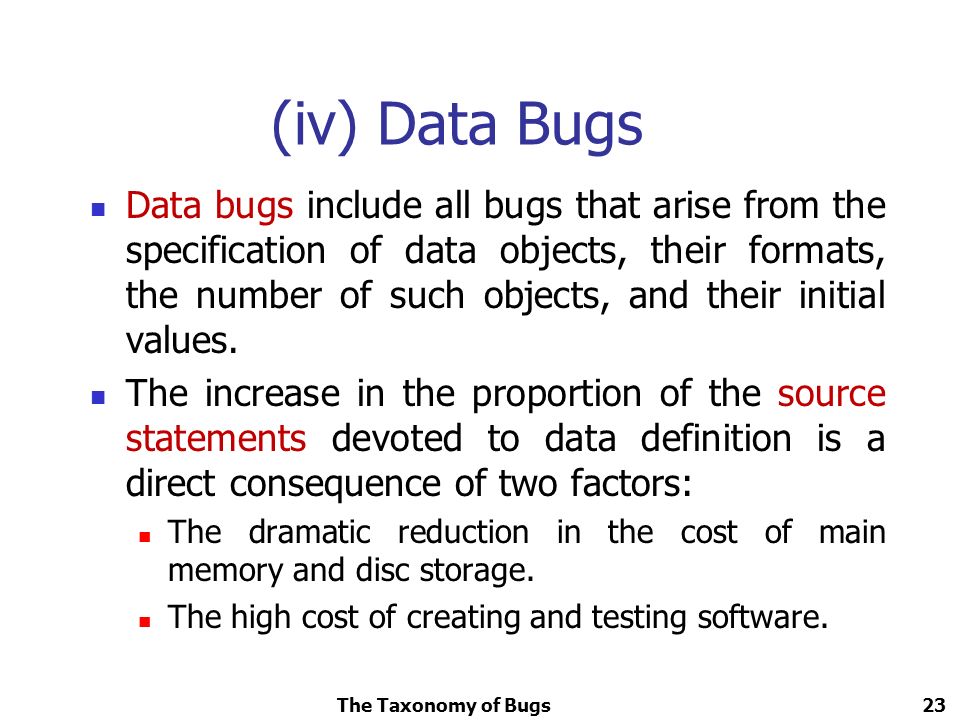
UNIT – I (b) THE TAXONOMY OF BUGS 1. The Consequences of BUGS The importance of Bugs depends on frequency, correction cost, installation cost and consequences. - ppt download

Amazon.com: Doing Bayesian Data Analysis: A Tutorial with R and BUGS: 8601300089751: John K. Kruschke: Books
Data analysis process: from bug tracking data to the prediction results. | Download Scientific Diagram




![PDF] Software Bug Detection using Data Mining PDF] Software Bug Detection using Data Mining](https://i1.rgstatic.net/publication/275327486_Software_Bug_Detection_using_Data_Mining/links/5537581d0cf268fd001898bb/largepreview.png)